CyberPoint Interns Learn Penetration Testing, Among Other Things
This post documents the actions taken by our summer interns at CyberPoint. We presented them with a series of questions and their answers are un-edited below (they were warned).
First, let's start with introductions. Who are you? First names are fine. What were the projects you executed this summer at CyberPoint International? Please give us descriptive answers, but in your own words for each project. You worked on three separate things, what were they?
Our names are Lucas, Davis, and Ehren, and we are rising seniors at Gilman School who interned at CyberPoint International this summer. We worked on three projects. The first project was using Yoda's Protector and UPX to pack various malware files. The second project was creating a cluster for the Bro Intrusion Detection System which would send alerts if it detected any suspicious traffic on the network. Our final project was to use CATO to do penetration testing on a customer's website.
For CATO, can you please describe it in your own terms? What does it do? Do not describe or reveal details of the target(s) you focused on, these are considered sensitive to you and your 'customer'. Instead, tell me what kinds of things you did to your targets?
CATO is an application created by CyberPoint that places all the tools that one would need to perform penetration testing on one website. CATO also organized the findings and placed them in a database where they could be reviewed by other members of the team and automatically assigned CVSS ratings (a scoring system for vulnerabilities related to how dangerous they were to the integrity, accessibility, and confidentiality of the information) to vulnerabilities. Using CATO, we performed different types of scans such as Nikto and OpenVAS. Additionally, we discovered more targets like other domain names and IP addresses associated with the one we originally found and performed more scans on those targets. Without such a simple interface like CATO, the process of scanning the website would have been much more difficult and tedious.

How much introduction did you get to CATO and how to use it? Did you find it difficult to use?
We did not get much introduction to CATO; however, we did not find it very difficult to use with the limited knowledge of it that we had.
Tell me something that you learned while working with CATO? Did you learn about a new tool? A way to analyze a target for vulnerabilities? The process of analyzing targets for vulnerabilities in the first place?
We came in knowing almost nothing about penetration testing, save for what it was. We learned about the methods and process of finding vulnerabilities and things like the kill chain attack approach. CATO definitely helped us put the knowledge we gained to action.
For your Bro Cluster, what was the goal of this effort? What did you understand you were trying to accomplish? What does Bro do?
The goal of creating the Bro Cluster was to learn about computer clusters, Intrusion Detection Systems, Linux, and different kinds of traffic. The goal for the Bro cluster started off by being able to recognize and send an alert for an Nmap scan, but gradually evolved to being able to recognize malware traffic. Bro is an intrusion detection system which sits on and monitors a network and creates notices for suspicious traffic and activities.
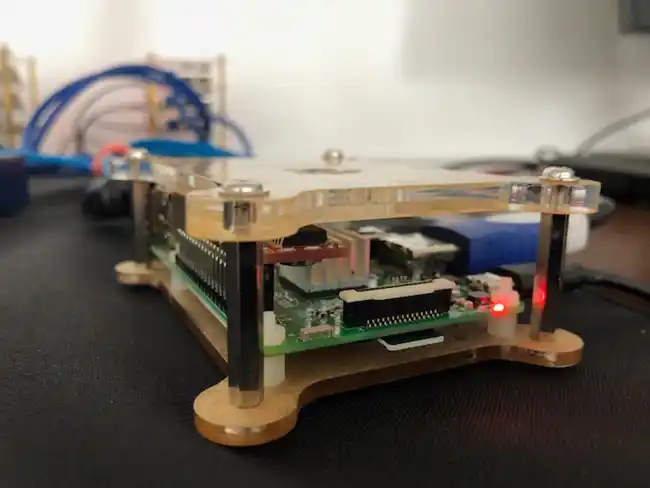
You switched operating systems on your Bro cluster node partway through, why was that?
We switched operations systems partway through building the cluster because we found that some of the software necessary was not completely compatible with the original operating system. We started using Raspbian Stretch, then switched to Arch Linux, and finally to Ubuntu Mate.
For your Bro Cluster, tell me what you learned about the individual hardware of your cluster platform? What was the name of the platform? Did you like working with it? Did you dislike it? What platform did you use and what did you learn about it?
We learned how to configure a Raspberry Pi with different distributions of Linux, the first single board computer any of us had worked with. We also made a stack structure for the boards, making the hardware and wires more organized. We used three different distributions of Linux: Raspbian, Arch Linux, and Ubuntu Mate. Raspbian, a platform based on Debian and probably the most well-known OS (Operating System) for Raspberry Pis, and Arch Linux, a Linux distribution without a desktop environment and that is relatively straightforward and easy to use, both were not working with PF_RING, an essential component to the operation of a Bro Cluster. Finally, we came upon Ubuntu Mate which did work with PF_RING, so this is the platform we finally decided to settle on using. Overall, it was not very hard to use because it worked very similarly to Ubuntu 16.0.4 LTS, a platform we were familiar with. With all of the distributions of Linux we worked with, we learned more about operating in the terminal.
If unanswered in your introduction, tell me what you did to try and get the Bro system to recognize and alert on your actions? You did at least 3 independent things on your two connected laptops.
We setup the Bro cluster to monitor traffic going between two laptops. From one of the laptops, we ran an Nmap port scan on the other, which triggered a notice on bro. The second thing we did on our laptop was using a pcap file (a file which captures packets that moved across a network) downloaded from the internet which acted like a piece of malware was running across the network. We used Tcprewrite to edit the file so that it appeared that it was coming from one laptop to the other originally, and then used Tcpreplay to send the packets across the network. This also registered an alert for bro. Finally, we set up one of the laptops to host a server which had the EICAR test file (a file universally agreed upon by antivirus software developers that registers as a piece of malware for the sake of testing) as a downloadable link on it. We connected to the server from the other laptop and downloaded the file over Ethernet, but this did not register an alert.
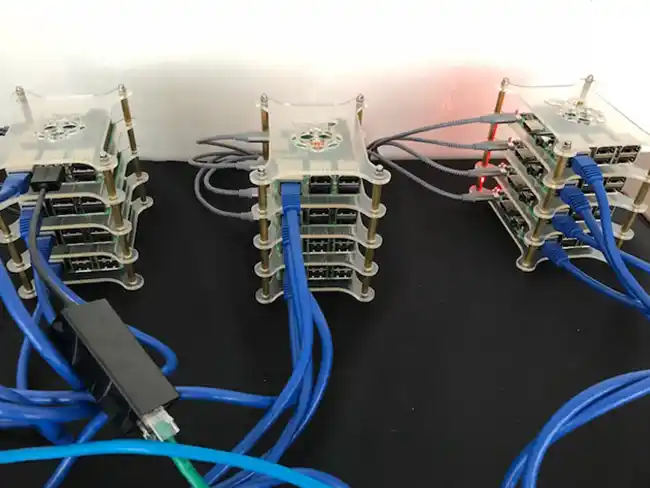
Do you believe you have successfully proven that work is being divided up amongst all nodes in your cluster?
We cannot conclusively say that work is being divided amongst all nodes in the cluster. Documentation for Bro suggests using a physical hardware device as a load balancer, but we instead used one of the raspberry pis as the frontend. We used Tcpdump on one of the worker nodes to see all the traffic that it was seeing and saw that the manager was communicating with it. Additionally, we found log files that suggest that work is divided, but when timing the difference between how long it takes to register a notice using only one node versus 12, we found that there was not a significant difference in the timing. We hypothesize that the nodes are indeed dividing the work, but there was not enough traffic for there to be a significant difference in timing. We think that the difference would become apparent if we had a significant increase in the amount of traffic.
Did you have fun?
Definitely.
About CyberPoint
At CyberPoint, we work to create a future where individuals and organizations from across the globe can operate safely and securely in cyberspace and benefit from the technological innovations that increasingly connect our world. A rapidly growing cybersecurity company, CyberPoint integrates and delivers innovative, leading-edge services, solutions, and products to protect what's invaluable to customers worldwide. We discover the threats and vulnerabilities that expose data, systems, and infrastructure to compromise, we quantify risks, and we design defenses that provide critical protection. Learn more here.