Traditional Perimeter Security and Zero Trust – Are they Really That Different?
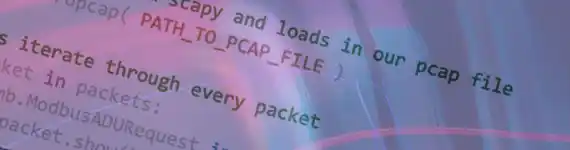
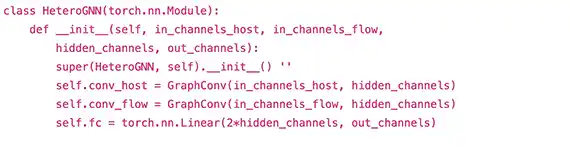
This post will compare and contrast of some differences between Zero Trust (ZT) based perimeter security and traditional perimeter security. It will not be possible to cover all differences or similarities, so the focus will be of some highlights. In particular, the focus will be on Artificial (and Automated) Intelligence (AI), automated system refresh capabilities, logging, and Virtual Private Networks (VPNs). Knowing that many organizations are utilizing Machine Learning and Artificial (and Automated) Intelligence today, it is likely there are organizations already implementing ZT capabilities. While AI/ML are not the only aspect of ZT, it is utilized in ways that extend the automation process and reduce response time to flagged events. As with all organization's security-based decisions, the cost to implement ZT capabilities must be a factor in determining the scope and feasibility of its coverage. For example, a company may have the ability and financial backing to integrate a moderate level of AI log analysis yet may not have the resources to implement automated responses to events.
Read More